To avoid abuse of email aliases, only the authorized staff have the access right to all-staff or all students email group alias.
It cannot be re-edited again. Please re-edit a new email and then set the scheduled sending. The previous scheduled email will be in the draft box, please delete it completely in time.
Because the Tencent Mail supports the client software to receive emails from the last 30 days by default, if you use Outlook, Foxmail, or mobile APP to receive emails through IMAP, POP, etc., please adjust the relevant options:
(1)Log in to the mailbox through a computer web browser, click [Set] - select [Client Settings]
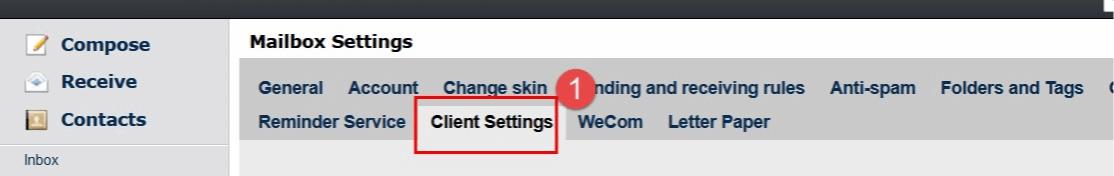
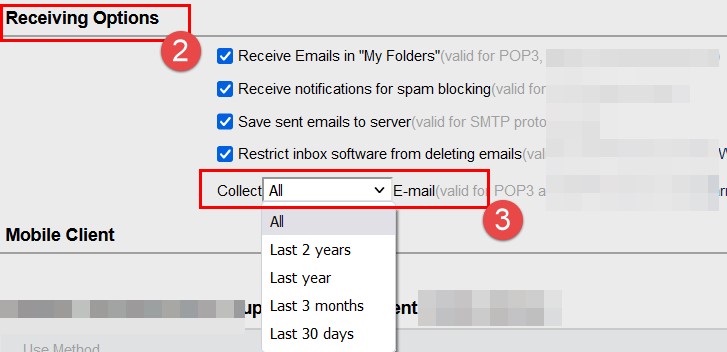
(2)In the Receiving Options, change the default to receive emails from the last 30 days to receive all emails
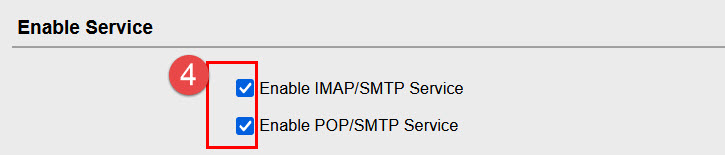
(3)On this client setup page, make sure the client receive mail option is enabled
The client device configured with IMAP or POP?
The main difference is that IMAP(Internet Messaged Access Protocol) always syncs with mail server so that any changes you make in your mail client (Microsoft Outlook, mobile phone) will instantly appear on your webmail inbox.On the other hand, in POP(Post Office Protocol), your mail client account and mail server are not synced.For example, Outlook must use the IMAP protocol to connect the mailbox to achieve folder synchronization.
How to check email calendar on mobile phone?
You can install Tencent's QQ Mail APP(QQ邮箱APP)through the mobile application market (after installation, go to Settings-Application-Turn on the sync Tencent mailbox calendar function)
What is Phishing?
Phishing is a type of online scam where criminals send an email that appears to be from a
colleague, friend, family member and ask you to provide sensitive information. This is usually
done by including a link that will appear to take you to the company’s website to fill in your
information – but the website is a clever fake and the information you provide goes straight to
the crooks behind the scam.
What is the danger of phishing?
Phishing is one of the most dangerous forms of cybercrime because, for the most part, it can’t be
detected by regular antivirus software.
Once the individual or organization behind the phishing scam has your personal information, you
are in danger of falling victim to identity theft, which has serious consequences for financial
stability and credit, or even political harm.
How to identify a phishing emails?
1) Check the sender's email address—if looks suspicious, don’t open the email. Don’t trust the
display name as the phishing email is often forged a name, such as a system administrator
account or the company name.
2) Check the recipient’s address. If you find that the email is sent to large number of employee
in different departments. It may be a phishing email.
3) Check the email sending time. If it beyond working hours, like 3:00am, you need to be
vigilant about it.
4) Check the email subject. Most of phishing emails using "system administrator",
"notification", "purchase order", "invoice", "conference schedule", "list of participants", "review
of previous conferences", etc. as the subject.
5) Be alert to emails that use generic greetings such as Dear User, Dear Colleague. At the same
time, be alert to any email that creates an emergency atmosphere. For example "Please be sure to
complete it today". Most phishing emails attempt to create a sense of urgency, leading recipients
to fear that their account is in jeopardy or they will lose access to important information if they
don’t act immediately.
6) Legitimate banks and most other companies will never ask for personal credentials via
email. Don’t give them up.
7) Be aware of the Emails with spoofed links. Also, look for URLs including "&redirect" ,it
may be a phishing email. Be aware of the "Unsubscribe" button, some of them are leading to
more spam after clicking, or be implanted with malicious code. You can directly block the spam
sender's email address.
8) Use caution when opening email attachments, even if they appear to be from someone you
know. Scan the file using your antivirus program before opening it. Files such as word, pdf,
excel, PPT, rar, etc. may be embedded with Trojans or spyware, especially executable files
with .exe and .bat suffixes in the attachment.
